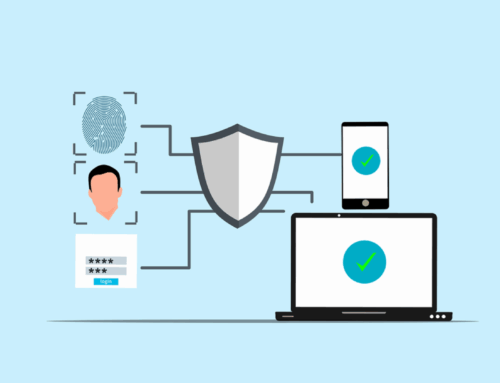
Cyber hygiene ensures your enterprise is protected against treacherous cyber-attacks and threats like malware, data theft, phishing, and more.
Cyber hygiene is the need of the hour as the work-from-home scenario has opened doors to more targeted, dangerous, and frequent threats than ever. Employees now rely on their home or public network, often using personal devices, compared to working from within the secure parameters of the office where firewalls and instantaneous tech support protect devices and networks. This has made enterprises more vulnerable to cyber-threats, and the rate of attacks have spiraled. Businesses must increasingly investigate how to prevent data breaches.
The question that keeps IT professionals up at night is: how do you ensure good cyber hygiene even during the most uncertain times?
Luckily, the first step towards achieving cyber hygiene is quite simple: maintaining good cyber hygiene practices.
6-Point Checklist
1. Use Multi-factor Authentication
Multi-factor authentication involves adding layers of security to verify a user’s identity while logging in or carrying out other transactions. In general, passwords are the first level of authentication, followed by a security token and then a biometric verification, facial or fingerprint recognition.
The idea is to make it more difficult for anyone to break in and get access by adding multiple security protocols to incorporate identity and access management. We explore MFA in more depth for small/medium businesses in this blog post.
2. Keep everything up to date
This goes for all your software updates, system upgrades, or essentially any kind of installation your system undergoes.
Updates are a crucial part of keeping your computer secure. As new vulnerabilities are discovered and fixed, developers issue updates to patch those vulnerabilities, fixing the loopholes. Thus, applying those updated patches as soon as possible is critical. If you don’t install software updates, you’ll be vulnerable to malware that may exploit these vulnerabilities.
Some operating systems offer automatic updates that automatically install themselves when they become available. A safer alternative would be to check for updates or install them manually after they become available. This helps prevent data breaches from occurring.
3. Have a data backup and recovery system
Companies produce large volumes of data almost every day. We’re talking consumer data, employee data, or system data – losing any of it can be crippling to a company.
Everything from files, folders, photos, payment data, delivery information, vendor data, customers’ data, account information, interactions, and even data from third-party apps should be backed up on external devices or the cloud.
It helps you prepare for unforeseen circumstances such as theft, system damage or failure, or natural disasters.
4. Keep an extra eye on phishing attempts
Phishing attempts can be difficult to spot, especially when they’re well executed. For example, you could receive an email asking you to click on a link or open an attachment that looks legitimate. In fact, the email may come from someone you know who’s been hacked and is being used as part of a phishing attempt.
Be wary of any requests for personal information, and always check that an email is legitimate before clicking on any links or attachments in it. In addition, double-check the URL of any sites you visit; if something looks off, don’t trust it!
5. Implement security protocols for VPNs
Mask your device’s IP address with end-to-end encryption using a VPN, which you can either install in your system or connect to through your web browser.
Verifying that your VPN is installed on all your devices is essential. You can have a home router with a built-in VPN that can be used for all your home devices.
Alternatively, you may also have an app for your smartphone or tablet that provides the same functionality via an encrypted connection to a server hosted by the provider.
6. Keep vulnerability checks in order
While you’re maintaining precautions to prevent mishaps, checking regularly for loose ends is a good practice.
Take a deeper look at any red flags your security program might have highlighted, check if they’re positive, and determine their severity and impact. If there is a problem, take immediate action to address it.
Meanwhile, record how long it took for you and your team to analyze pieces of forensic data and fix the problem. It helps knowing how much time you have until attackers break into your system and how you can optimize your processes.
Best practices while working from home
Now that you’ve seen the checklist, below are some best practices to follow when working remotely. Post-pandemic, many companies continue to offer their employees great flexibility in working models like remote or hybrid working.
This scenario calls for setting clear goals ahead of time and encouraging any remote or hybrid employees to follow preventive measures to protect your enterprise.
- Use a secure connection. Use a private network or a home internet connection. Refrain from using any unsecured public Wi-Fi hotspot.
- Don’t leave devices unattended when they’re plugged into public outlets, especially if those outlets are visible from outside windows or doors.
- Use a secure network. Keep in mind that this should be done through HTTPS protocol (and not HTTP), and be aware of who all are connecting and what they are accessing using this network.
- Keep passwords unique and change them periodically. Pick a strong password, use a combination of upper-case letters, lower-case letters, and numbers in different orders for each account, or use any online password-generating tool.
- Have anti-virus software installed to detect any potentially harmful content in your system and upgrade it regularly.
Key Takeaway
Practicing good cyber hygiene doesn’t necessarily guarantee complete protection against attacks, but it certainly improves your security settings and helps prevent data breaches. This is why businesses need to have a concrete cybersecurity plan in place as we continue to move forward in a post-pandemic world.